L2TP Split Tunneling Control
The default behavior for a Microsoft L2TP VPN add a new default route for the VPN connection and modifies the existing default route to have a higher metric, this causes all traffic to be forced through the VPN Tunnel. You have a couple of option depending on what the clients need to actually access.
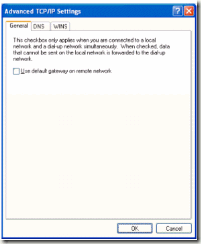
1. To access only devices on the VPN destination subnet over the tunnel you can disable the “Use default gateway on remote network†option. Select Internet Protocol (TCP/IP) on the Networking tab for the properties of the VPN connection. Click Properties, and then click Advanced. In Advanced TCP/IP Settings, on the General tab, clear the Use default gateway on remote network check box.
2. If additional network need to be reachable you can add manual routes using a .cmd file or other method. The route commands need to use the IP address that is dynamically assigned during the connection to the VPN client computer (by the VPN server) as the gateway IP address.
Example Command: route add 10.0.0.0 mask 255.0.0.0 [Client IP]
Split-tunneling Security Issues
When a VPN client computer is connected to both the Internet and a private intranet and has routes that allow reachability to both networks, the possibility exists that a malicious Internet user might use the connected VPN client computer to reach the private intranet through the authenticated VPN connection. This is possible if the VPN client computer has IP routing enabled. IP routing is enabled on Windows XP-based computers by setting the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\ Services\Tcpip \Parameters\IPEnableRouter registry entry to 1 (data type is REG_DWORD).
If you must use split tunneling, you can help prevent unwanted traffic from the Internet by doing the following:
Use the Network Access Quarantine Control feature in Windows Server 2003 to check whether connecting VPN clients have IP routing enabled and, if so, do not allow VPN access until it has been disabled. Use IP packet filters on the VPN remote access policy profile to discard both inbound traffic on the VPN connection that has not been sent from the VPN client and outbound traffic that is not destined to the VPN client. The default remote access policy named Connections to Microsoft Routing and Remote Access server in Windows Server 2003 has these packet filters configured by default.